Integrate Microsoft Entra Groups with Keycloak Composite Roles
This page describes how to integrate Microsoft Entra Groups with Keycloak Composite Roles to simplify the Keycloak identity provider configuration.
Note
Azure Active Directory is now known as Microsoft Entra ID.
This is an optional post deployment step.
Prerequisites
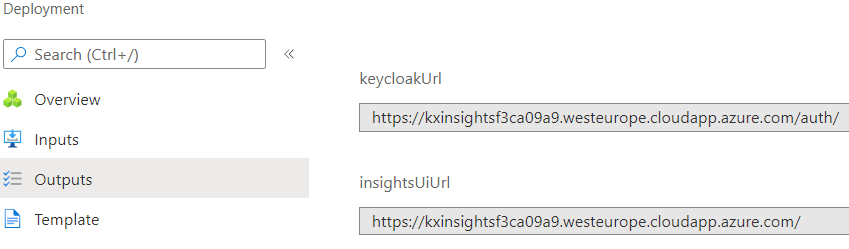
To successfully create composite roles in Keycloak, you need the Keycloak admin password and URLs of your kdb Insights Enterprise deployment.
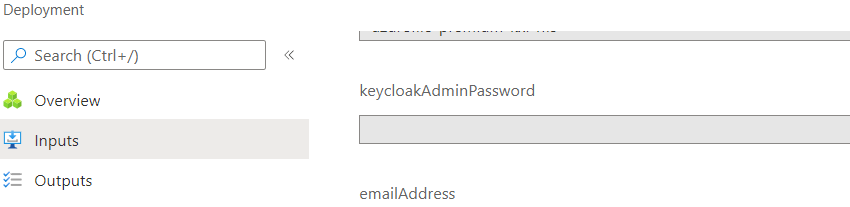
Create kdb Insights Enterprise composite roles
kdb Insights Enterprise uses Keycloak as its Identity and Access Management component.
Follow the steps below to log into Keycloak and create the necessary roles.
-
Use the
keycloakUrlor theinsightsUiUrl+/auth/from the Prerequisites section to navigate to the Keycloak web UI. -
Click Administration Console and log in with the username
userand the password you provided during the deployment.
-
Choose the Insights target realm from the top-left realm drop-down.
-
Click Roles in the left-hand menu, and then click the Add Role button.
-
Enter the Role Name: <role name> and click Save.
-
Turn Composite Roles ON.
-
Associate it with the desired roles.